Analyzes, informs, and makes decisions independently if needed
In today's digital world, cyber threats are constantly evolving and can affect businesses of any size.
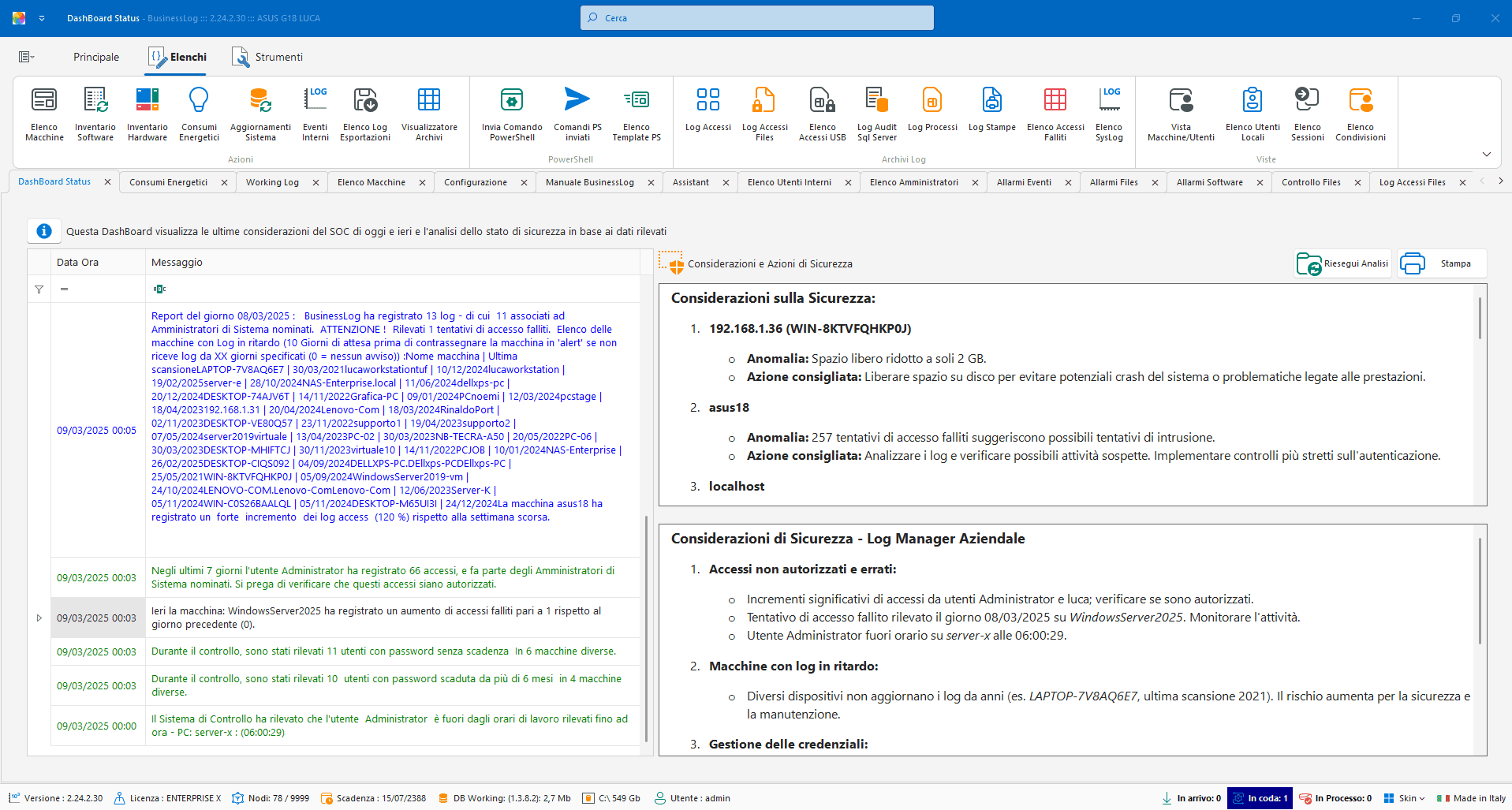
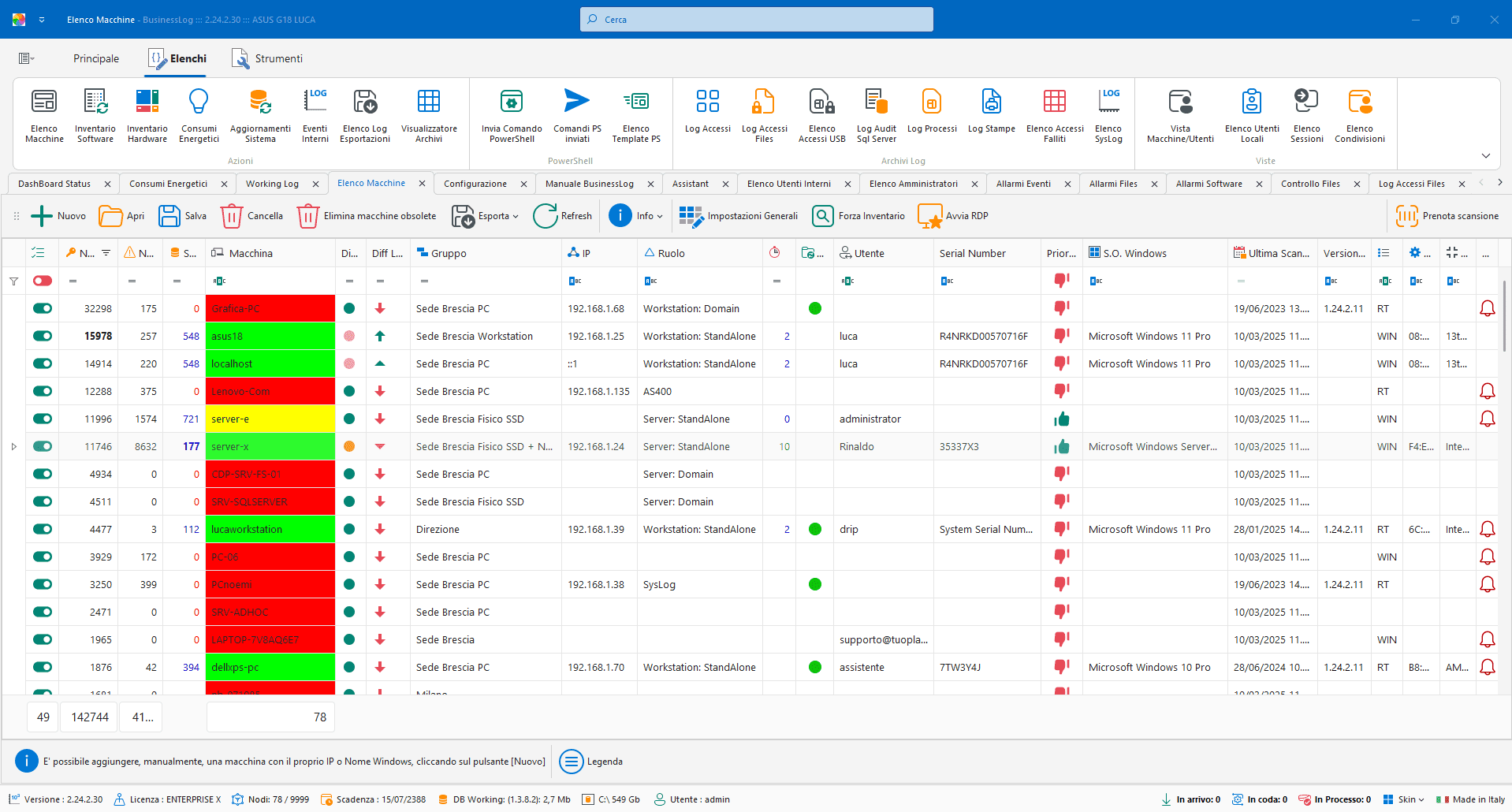
In addition to the classic capabilities of a Security Operation Center (SOC), the version integrated into Business LOG offers advanced capabilities for event analysis, automatic correlation, and continuous monitoring of user behavior.

GDPR Compliance

NIS2 Compliance

ISO 27001 Compliance

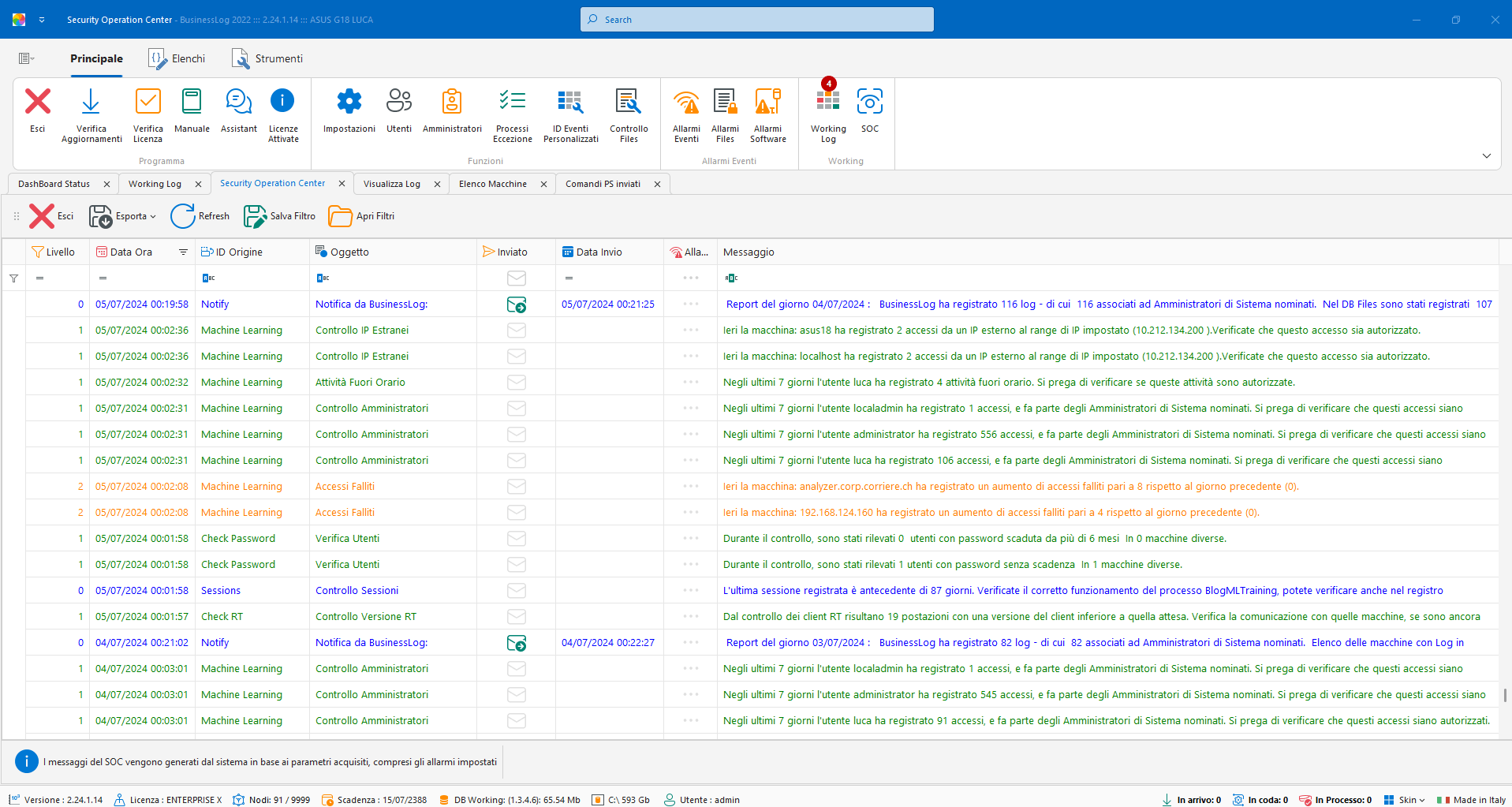
Business LOG - Alarm detected!
Business LOG has registered an alarm ....
The daily report is available...

Real-time detection
Business LOG’s Security Operation Center (SOC) detects and responds to cyber threats in real time, ensuring continuous protection against attacks, vulnerabilities, and suspicious activities, with immediate mitigation actions.
With constant 24/7 monitoring and advanced behavioral analysis tools, it can prevent incidents before they become critical, providing proactive and reliable security.
Proactive security
Constant monitoring 24/7
Behavioral analysis tools
Fast response to incidents
In the event of an issue, Business LOG's SOC can immediately activate response procedures to contain and mitigate the impact.
This includes isolating threats, repairing compromised systems, and restoring normal operations as quickly as possible. Business LOG's Alerts system is able to prepare commands that can promptly intervene and learn to prevent future security problems.
Instant response to threats
Repair and restoration
Prevention of future problems

Request a quote now
Request a Business LOG quote parameterized to your organization's actual needs.
Proactive threat analysis
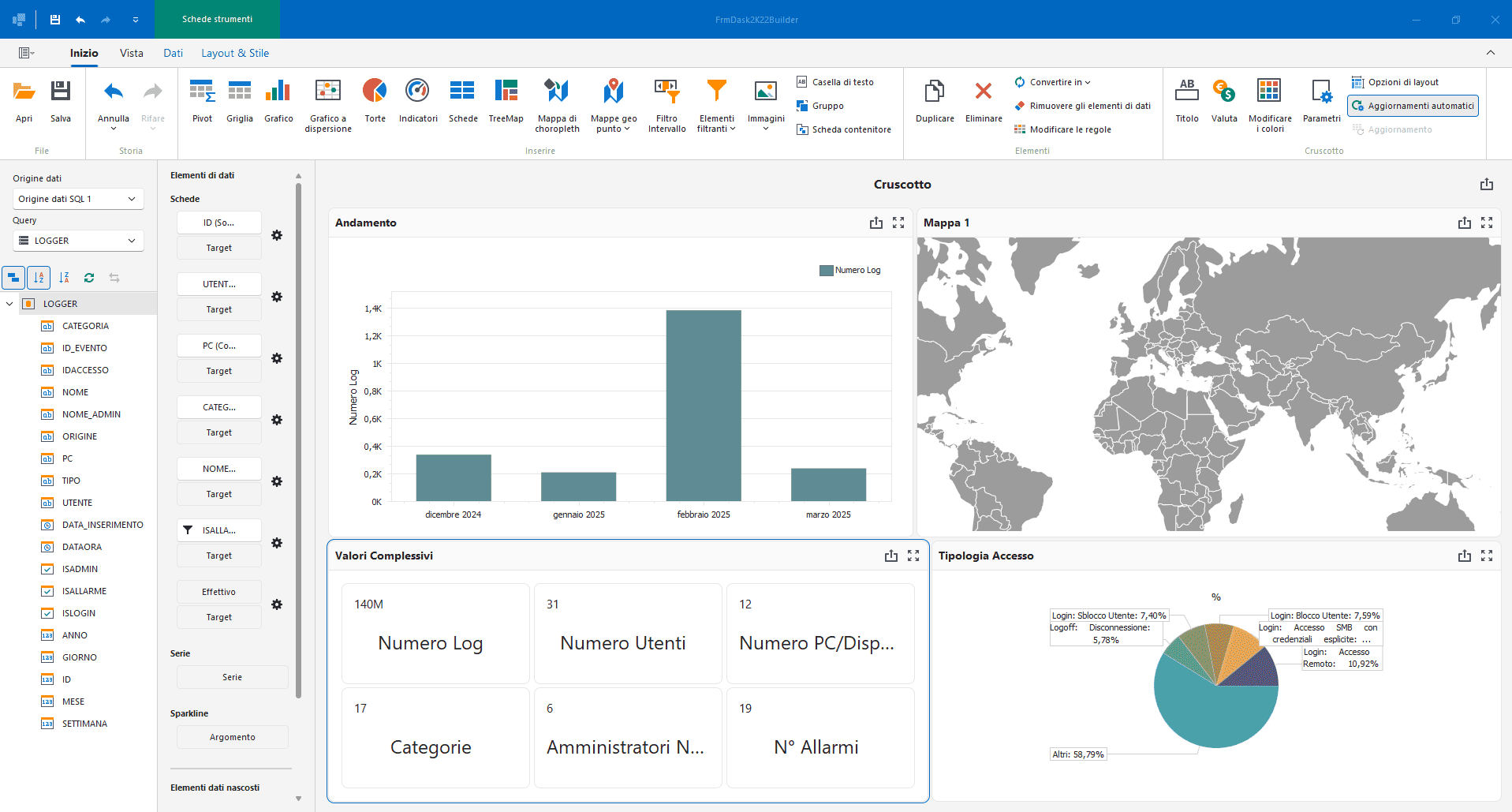
Using intelligence tools, machine learning and artificial intelligence-based data analysis, the SOC can predict potential attacks and vulnerabilities.
This proactive approach allows preventive measures to be taken before major incidents occur. In addition, with the ability to analyse large volumes of data in real time, the SOC also detects complex and targeted threats that are difficult to detect using traditional methods. This provides advanced protection and the ability to quickly adapt to new types of attacks, improving the overall resilience of the organisation.
Proactive attack prevention
Real-time data analysis
Adaptation to new threats
Regulatory compliance
The Security Operation Center helps your organization maintain compliance with data security regulations, such as GDPR, NIS2 and many more. Provides detailed reports and audits that demonstrate adherence to industry laws and standards.
This reduces the risk of penalties and protects your corporate reputation, providing a solid foundation for managing compliance audits and improving overall business data security.
GDPR Compliance
NIS2 Compliance
ISO 27001 Compliance
Request a quote now
Request a Business LOG quote parameterized to your organization's actual needs.
Training and awareness
In addition to the technical aspects, the SOC provides tools to raise staff awareness of best safety practices, reducing the risk of human error. Through early warning and alert notifications, staff are informed about potential threats and risky behaviors.
This proactive approach helps to improve the internal incident response and strengthens the safety culture within the company, Ensuring that all employees are aligned with security policies and adopt appropriate behaviors to prevent attacks.
Awareness of staff
Timely notifications and alerts
Safety culture
Custom alarms and reports
Set up alerts specific to your business needs and receive detailed reports on suspicious activities. Alarms can be set for various conditions, such as unauthorized access, critical file changes or anomalies in user behavior.
Reports provide a comprehensive overview, allowing you to analyze events in detail and make informed decisions to improve your business security. These reports can also be easily shared with management or used for security compliance audits.
Custom alarms
Detailed reports
Management tools

System Administrators.
With constant monitoring and automatic event correlation, the SOC supports System Administrators in network management and rapid threat resolution, improving operational security.
Chief Information Security Officer (CISO).
The Business LOG SOC provides the Chief Information Security Officer with continuous visibility into potential threats and vulnerabilities, facilitating the establishment of effective security strategies and proactive incident management.
Chief Executive Officers (CEO).
The SOC provides CEOs with continuous protection against cyber attacks, reducing risk to the business and ensuring business continuity and safeguarding corporate reputation.
Compliance Officer.
The SOC facilitates regulatory compliance through detailed reports and audits, ensuring that the company complies with GDPR, NIS2 and other regulations, simplifying the work of verification and certification.
Legal Departments.
The SOC provides detailed documentation on threat management and regulatory compliance, helping to avoid penalties and prove adherence to data security laws.
IT Managers.
The SOC ensures 24/7 protection and provides advanced tools to prevent attacks, enabling IT managers to maintain systems integrity and reduce downtime.
Through the SOC Stream Plugin it is possible to consult the information collected by the SOC (installed on-premise) on a dedicated website, thus ensuring a complete view, always available and in real time of security and compliance activities.
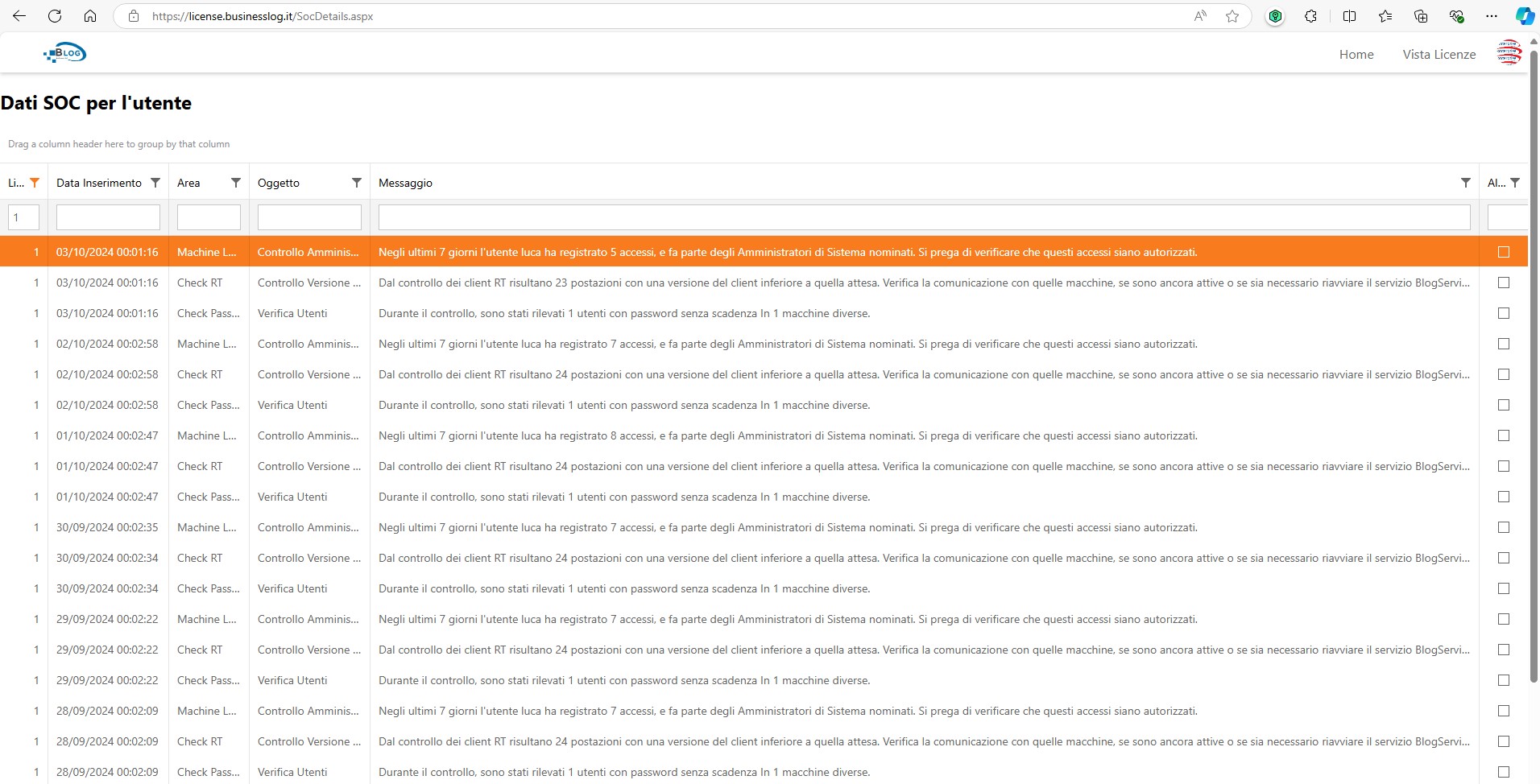
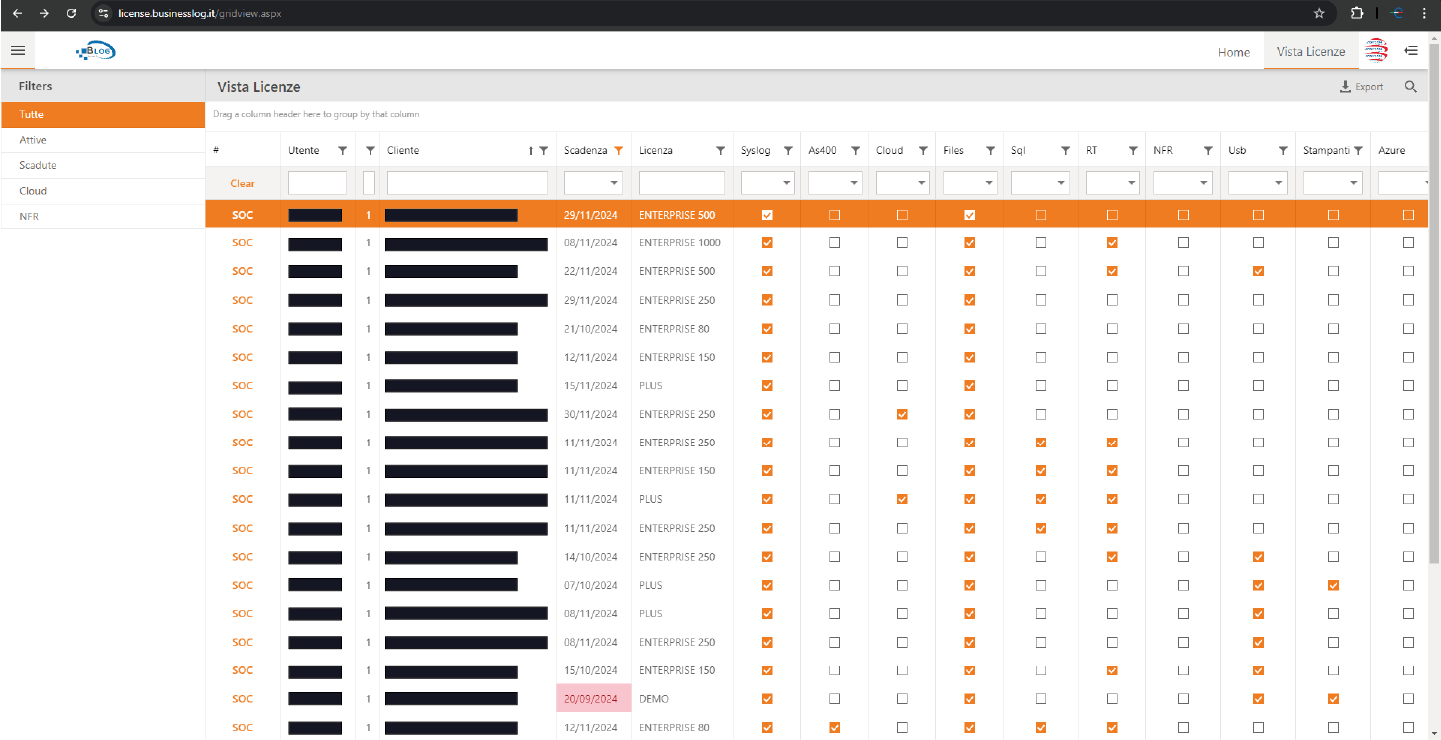
By swiping to the left, you can see what the SOC Stream Plugin shows to Business Partners LOG (that is a control panel with all its customers' SOCs, from which it can access individual views), while scrolling to the right, You can see the interface reserved for Business LOG customers.
Find out all the key answers about Business LOG Server.
Request a Business LOG Quote
Are you interested in the Suite? Request a Business LOG quote now to evaluate the opportunity for your organization